Gotcha!
Your IP: 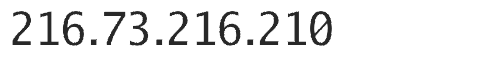
Your Browser: 
Your OS: 
Your Trapper's summary banner:
Place http://trapper.io/banner on your website for free to show users that you know who they are
*Note: in this free version of Trapper you may only see things that differentiate your fingerprint from others.
Canvas
OpenGL
Video
etc. -not now
*Note: in this free version of Trapper you may only see things that differentiate your fingerprint from others.
Browser's fingerprint detailed view
About Trapper.io

Website Fingerprinting and Anonymous Fingerprinting may expose more of your information than you think!
 Do you ever wonder just how much of your information or activity is available online for the world to see? Thanks to website fingerprinting and anonymous fingerprinting there are many ways that you may be vulnerable. Like with any leak you have to find the holes if you hope to anonymize and prevent further damage.
We all know that there is some tracking done when we log into a website. Just think about the ads you see when you are done browsing and you go to your social media page or to your email for example. Oftentimes there will be something related to the very thing you just got done looking at. What you may not know is that tracking networks actually create entire profiles of the normal activities taking place on your browser. Over time this information builds up, and this could be taking place on multiple tracking networks.
While this type of tracking is generally used for advertising as earlier discussed, every now and then it could be used maliciously. Have you ever logged onto a site, signed up for something or the like and had your phone begin ringing off the hook by telemarketers? Well, you were tracked, and enough information was left behind to be sold. The scary thing is that these tracking websites produce accuracy rates of up to 94%! Knowing how to anonymize your information and history is vital in today's fast paced digital era.
Do you ever wonder just how much of your information or activity is available online for the world to see? Thanks to website fingerprinting and anonymous fingerprinting there are many ways that you may be vulnerable. Like with any leak you have to find the holes if you hope to anonymize and prevent further damage.
We all know that there is some tracking done when we log into a website. Just think about the ads you see when you are done browsing and you go to your social media page or to your email for example. Oftentimes there will be something related to the very thing you just got done looking at. What you may not know is that tracking networks actually create entire profiles of the normal activities taking place on your browser. Over time this information builds up, and this could be taking place on multiple tracking networks.
While this type of tracking is generally used for advertising as earlier discussed, every now and then it could be used maliciously. Have you ever logged onto a site, signed up for something or the like and had your phone begin ringing off the hook by telemarketers? Well, you were tracked, and enough information was left behind to be sold. The scary thing is that these tracking websites produce accuracy rates of up to 94%! Knowing how to anonymize your information and history is vital in today's fast paced digital era.
Let's look at some of the ways you are being tracked online.
 Your IP address is your digital fingerprint. This is your identification, your digital DNA if you will. Now the IP address can share with other devices connected in your home or office, but in all it leads straight back to your browser activities and those devices in your home or office. This address will lead these tracking sites to your location right down to the city and state. Again, this is commonly used for ads that are relative to your location, but in the wrong hands... well you can imagine how that could turn out.
When using the IP address in unison with other tracking methods like HTTP Referrer things get even more transparent. HTTP Referrer is what happens when you click a link and the site you are leaving tells the site you are entering where you just came from. This information is contained in the header. It is sent over when the page loads.
Did you know that we are infested with web bugs! Sure we are! These one pixel images are invisible to the naked eye, but they are there. Not only do they utilize the HTTP Referrer but they also track your opened emails containing images.
Your IP address is your digital fingerprint. This is your identification, your digital DNA if you will. Now the IP address can share with other devices connected in your home or office, but in all it leads straight back to your browser activities and those devices in your home or office. This address will lead these tracking sites to your location right down to the city and state. Again, this is commonly used for ads that are relative to your location, but in the wrong hands... well you can imagine how that could turn out.
When using the IP address in unison with other tracking methods like HTTP Referrer things get even more transparent. HTTP Referrer is what happens when you click a link and the site you are leaving tells the site you are entering where you just came from. This information is contained in the header. It is sent over when the page loads.
Did you know that we are infested with web bugs! Sure we are! These one pixel images are invisible to the naked eye, but they are there. Not only do they utilize the HTTP Referrer but they also track your opened emails containing images.
Tracking scripts and cookies are well known culprits used to track out history and information online, but did you know they also leave you exposed!
 While you are leaving behind bits and pieces of your online identity and interests websites are also planting small tidbits of information in your browser. Let's say that you do a lot of online banking. Every time you log in it is the cookies that remember the information used to do so. These are also responsible for website changes and tracking your activity across the internet. If that's not enough, cookies also identify you. While it is not a problem usually, when third party cookies become involved it becomes a lot more damaging.
Don’t get me wrong, third party cookies do have their purpose which is normally related to advertising. When it comes to super cookies it gets a little harrier. This is because you can always clear your browsing data and cookies. With super cookies it's not as simple as that. This type of "cookies" is becoming more common. These, like ever cookies, store in multiple locations. If it is found that a part of a super cookie has been deleted it will resurface from another stored location.
Here is a little something that you may not know. Each time we log on to a site there is a user agent that is sent out from the browser. The purpose here is so that sites know the OS you are using in order to give you the optimal user experience while also ad targeting hence even more data is stored.
While you are leaving behind bits and pieces of your online identity and interests websites are also planting small tidbits of information in your browser. Let's say that you do a lot of online banking. Every time you log in it is the cookies that remember the information used to do so. These are also responsible for website changes and tracking your activity across the internet. If that's not enough, cookies also identify you. While it is not a problem usually, when third party cookies become involved it becomes a lot more damaging.
Don’t get me wrong, third party cookies do have their purpose which is normally related to advertising. When it comes to super cookies it gets a little harrier. This is because you can always clear your browsing data and cookies. With super cookies it's not as simple as that. This type of "cookies" is becoming more common. These, like ever cookies, store in multiple locations. If it is found that a part of a super cookie has been deleted it will resurface from another stored location.
Here is a little something that you may not know. Each time we log on to a site there is a user agent that is sent out from the browser. The purpose here is so that sites know the OS you are using in order to give you the optimal user experience while also ad targeting hence even more data is stored.
You can even be tracked through screen resolution and time zone!
 Browser fingerprinting is very commonly used to track you, gain information and store information as well. Browsers are unique to their user. I mean, you customize it and make it your own. When researched I found out that only around a million people actually have the same browser configurations that I have. That’s not a lot considering how many people have custom browsers.
What it all comes down to is money, and a lot can be found in tracking. These website fingerprinting and anonymous fingerprinting methods are becoming more and more sophisticated. Staying in the know is essential to protecting your information and privacy. This is the only way you can even begin that to anonymize it. Utilizing a website to help you do that is the only way to know where the holes are and fix them before your information falls into the wrong hands.
Don’t sit around wondering what the world knows about you or what may be lurking in the pixels. Take control by finding out what is leaking and how to anonymize it! Our website shows you all the leaking information which in return will help you find out a little more about your exposure to the outside world.
Browser fingerprinting is very commonly used to track you, gain information and store information as well. Browsers are unique to their user. I mean, you customize it and make it your own. When researched I found out that only around a million people actually have the same browser configurations that I have. That’s not a lot considering how many people have custom browsers.
What it all comes down to is money, and a lot can be found in tracking. These website fingerprinting and anonymous fingerprinting methods are becoming more and more sophisticated. Staying in the know is essential to protecting your information and privacy. This is the only way you can even begin that to anonymize it. Utilizing a website to help you do that is the only way to know where the holes are and fix them before your information falls into the wrong hands.
Don’t sit around wondering what the world knows about you or what may be lurking in the pixels. Take control by finding out what is leaking and how to anonymize it! Our website shows you all the leaking information which in return will help you find out a little more about your exposure to the outside world.
Trapper.io Acceptable Use Policy for fingerprint detection and other services

Why is Trapper.io providing this Policy to me?
Trapper.io goal is to provide its customers with the best fingerprint detection services possible. In order to help accomplish this, Trapper.io has adopted this Acceptable Use Policy (the “Policy”). This Policy outlines acceptable use of the Trapper.io, proxy IP and other services (the “Service”).
What obligations do I have under this Policy?
All Trapper.io fingerprint detection and other services customers and all others who use the Service (the “customer,” “user,” “you,” or “your”) must comply with this Policy. Your failure to comply with this Policy could result in the suspension or termination of your Service account and/or have you blocked from visiting this website and/or use any of the offered services. If you do not agree to comply with this Policy, you must immediately stop all use of the Service and notify Trapper.io so that it can close your account.
How will I know when Trapper.io changes this Policy and how do I report violations of it?
Trapper.io may revise this Policy from time to time by posting a new version on the Web site at http://www.Trapper.io or any successor URL(s) (the “Trapper.io Web site”). Trapper.io will use reasonable efforts to make customers aware of any changes to this Policy, which may include sending e-mail announcements or posting information on the Trapper.io Web site. Revised versions of this Policy are effective immediately upon posting. Accordingly, customers of the Trapper.io Services should read any Trapper.io announcements they receive and regularly visit the Trapper.io Web site and review this Policy to ensure that their activities conform to the most recent version. You can send questions regarding this Policy to, and report violations of it at, info (at) trapper (dot) io.
I. Prohibited Uses and Activities
What uses and activities does Trapper.io prohibit?
In general, the Policy prohibits uses and activities involving the Service that are illegal, infringe the rights of others, or interfere with or diminish the use and enjoyment of the Service by others. For example, these prohibited uses and activities include, but are not limited to, using the Service, Customer Equipment, or the Trapper.io Equipment, either individually or in combination with one another, to:
Conduct and information restrictions
- undertake or accomplish any unlawful purpose. This includes, but is not limited to, posting, storing, transmitting or disseminating information, data or material which is libelous, obscene, unlawful, threatening or defamatory, or which infringes the intellectual property rights of any person or entity, or which in any way constitutes or encourages conduct that would constitute a criminal offense, or otherwise violate any local, state, federal, or non-U.S. law, order, or regulation;
- post, store, send, transmit, or disseminate any information or material which a reasonable person could deem to be unlawful;
- upload, post, publish, transmit, reproduce, create derivative works of, or distribute in any way information, software or other material obtained through the Service or otherwise that is protected by copyright or other proprietary right, without obtaining any required permission of the owner;
- transmit unsolicited bulk or commercial messages commonly known as “spam;”
- send very large numbers of copies of the same or substantially similar messages, empty
messages, or messages which contain no substantive content, or send very large messages or files that disrupts a server, account, blog, newsgroup, chat, or similar service; - initiate, perpetuate, or in any way participate in any pyramid or other illegal scheme;
- participate in the collection of very large numbers of e-mail addresses, screen names, or other identifiers of others (without their prior consent), a practice sometimes known as spidering or harvesting, or participate in the use of software (including “spyware”) designed to facilitate this activity;
- collect responses from unsolicited bulk messages;
- falsify, alter, or remove message headers;
- falsify references to Trapper.io or its network, by name or other identifier, in messages;
- impersonate any person or entity, engage in sender address falsification, forge anyone else’s digital or manual signature, or perform any other similar fraudulent activity (for example, “phishing”);
- violate the rules, regulations, terms of service, or policies applicable to any network, server, computer database, service, application, system, or Web site that you access or use;
Technical restrictions
- access any other person’s computer or computer system, network, software, or data without his or her knowledge and consent; breach the security of another user or system; or attempt to circumvent the user authentication or security of any host, network, or account. This includes, but is not limited to, accessing data not intended for you, logging into or making use of a server or account you are not expressly authorized to access, or probing the security of other hosts, networks, or accounts without express permission to do so;
- use or distribute tools or devices designed or used for compromising security or whose use is otherwise unauthorized, such as password guessing programs, decoders, password gatherers, keystroke loggers, analyzers, cracking tools, packet sniffers, encryption circumvention devices, or Trojan Horse programs. Unauthorized port scanning is strictly prohibited;
- copy, distribute, or sublicense any proprietary software provided in connection with the Service by Trapper.io or any third party, except that you may make one copy of each software program for back-up purposes only;
- distribute programs that make unauthorized changes to software (cracks);
- use or run dedicated, stand-alone equipment or servers from the Premises that provide network content or any other services to anyone outside of your Premises local area network (“Premises LAN”), also commonly referred to as public services or servers. Examples of prohibited equipment and servers include, but are not limited to, e-mail, Web hosting, file sharing, and proxy services and servers;
- use or run programs from the Premises that provide network content or any other services to anyone outside of your Premises LAN, except for personal and non-commercial residential use;
- service, alter, modify, or tamper with the Trapper.io Equipment or Service or permit any other person to do the same who is not authorized by Trapper.io;
Network and usage restrictions
- restrict, inhibit, or otherwise interfere with the ability of any other person, regardless of intent, purpose or knowledge, to use or enjoy the Service (except for tools for safety and security functions such as parental controls, for example), including, without limitation, posting or transmitting any information or software which contains a worm, virus, or other harmful feature, or generating levels of traffic sufficient to impede others’ ability to use, send, or retrieve information;
- restrict, inhibit, interfere with, or otherwise disrupt or cause a performance degradation,
regardless of intent, purpose or knowledge, to the Service or any Trapper.io (or Trapper.io supplier) host, server, backbone network, node or service, or otherwise cause a performance degradation to any Trapper.io (or Trapper.io supplier) facilities used to deliver the Service; - resell the Service or otherwise make available to anyone outside the Premises the ability to use the Service (for example, through wi-fi or other methods of networking), in whole or in part, directly or indirectly. The Service is for personal and non-commercial residential use only and you agree not to use the Service for operation as an Internet service provider or for any business enterprise or purpose (whether or not for profit);
- connect the Trapper.io Equipment to any computer outside of your Premises;
- interfere with computer networking or telecommunications service to any user, host or network, including, without limitation, denial of service attacks, flooding of a network, overloading a service, improper seizing and abusing operator privileges, and attempts to “crash” a host; and
- accessing and using the Service with anything other than a dynamic Internet Protocol (“IP”) address that adheres to the dynamic host configuration protocol (“DHCP”). You may not configure the Service or any related equipment to access or use a static IP address or use any protocol other than DHCP unless you are subject to a Service plan that expressly permits you to do so.
II. Customer Conduct and Features of the Service
What obligations do I have under this Policy?
In addition to being responsible for your own compliance with this Policy, you are also responsible for any use or misuse of the Service that violates this Policy, even if it was committed by a friend, family member, or guest with access to your Service account. Therefore, you must take steps to ensure that others do not use your account to gain unauthorized access to the Service by, for example, strictly maintaining the confidentiality of your Service login and password. In all cases, you are solely responsible for the security of any device you choose to connect to the Service, including any data stored or shared on that device. It is also your responsibility to secure the Customer Equipment and any other Premises equipment or programs not provided by Trapper.io that connect to the Service from external threats such as viruses, spam, bot nets, and other methods of intrusion.
Commercial use and activity through our network are legal, but Trapper.io doesn’t hold any liability for it’s customers.
How does Trapper.io address inappropriate content and transmissions?
Trapper.io reserves the right to refuse to transmit or post, and to remove or block, any information or materials, in whole or in part, that it, in its sole discretion, deems to be in violation of Sections I or II of this Policy, or otherwise harmful to Trapper.io network or customers using the Service, regardless of whether this material or its dissemination is unlawful so long as it violates this Policy. Neither Trapper.io nor any of its affiliates, suppliers, or agents have any obligation to monitor transmissions or postings (including, but not limited to, e-mail, file transfer, blog, newsgroup, and instant message transmissions as well as materials available on the Personal Web Pages and Online Storage features) made on the Service. However, Trapper.io and its affiliates, suppliers, and agents have the right to monitor these transmissions and postings from time to time for violations of this Policy and to disclose, block, or remove them in accordance with this Policy, the Subscriber Agreement, and applicable law.
What requirements apply to electronic mail?
The Service may not be used to communicate or distribute e-mail or other forms of communications in violation of Section I of this Policy. As described below in Section III of this Policy, Trapper.io uses reasonable network management tools and techniques to protect customers from receiving spam and from sending spam (often without their knowledge over an infected computer)
Trapper.io is not responsible for deleting or forwarding any e-mail sent to the wrong e-mail address by you or by someone else trying to send e-mail to you. Trapper.io is also not responsible for forwarding e-mail sent to any account that has been suspended or terminated. This e-mail will be returned to the sender, ignored, deleted, or stored temporarily at Trapper.io sole discretion. In the event that Trapper.io believes in its sole discretion that any subscriber name, account name, or e-mail address (collectively, an “identifier”) on the Service may be used for, or is being used for, any misleading, fraudulent, or other improper or illegal purpose, Trapper.io (i) reserves the right to block access to and prevent the use of any of these identifiers and (ii) may at any time require any customer to change his or her identifier. In addition, Trapper.io may at any time reserve any identifiers on the Service for Trapper.io own purposes. In the event that a Service account is terminated for any reason, all e-mail associated with that account (and any secondary accounts) will be permanently deleted as well.
What requirements apply to instant, video, and audio messages?
Each user is responsible for the contents of his or her instant, video, and audio messages and the consequences of any of these messages. Trapper.io assumes no responsibility for the timeliness, mis-delivery, deletion, or failure to store these messages. In the event that a Service account is terminated for any reason, all instant, video, and audio messages associated with that account (and any secondary accounts) will be permanently deleted as well.
What requirements apply to personal web pages and file storage?
As part of the Service, Trapper.io provides access to personal Web pages and storage space through the Personal Web Pages and Online Storage features (collectively, the “Personal Web Features”). You are solely responsible for any information that you or others publish or store on the Personal Web Features. You are also responsible for ensuring that all content made available through the Personal Web Features is appropriate for those who may have access to it. For example, you must take appropriate precautions to prevent minors from receiving or accessing inappropriate content. Trapper.io reserves the right to remove, block, or refuse to post or store any information or materials, in whole or in part, that it, in its sole discretion, deems to be in violation of Section I of this Policy. For purposes of this Policy, “material” refers to all forms
of communications including text, graphics (including photographs, illustrations, images, drawings, logos), executable programs and scripts, video recordings, and audio recordings. Trapper.io may remove or block content contained on your Personal Web Features and terminate your Personal Web Features and/or your use of the Service if we determine that you have violated the terms of this Policy.
III. Network Management and Limitations on Data Consumption
Why does Trapper.io manage its network?
Trapper.io manages its network with one goal: to deliver the best possible fingerprint detection experience to all of its customers. High-speed bandwidth and network resources are not unlimited. Managing the network is essential as Trapper.io works to promote the use and enjoyment of the Internet by all of its customers. The company uses reasonable network management practices that are consistent with industry standards. Trapper.io tries to use tools and technologies that are minimally intrusive and, in its independent judgment guided by industry experience, among the best in class. Of course, the company’s network management
practices will change and evolve along with the uses of the Internet and the challenges and threats on the Internet.
The need to engage in network management is not limited to Trapper.io. In fact, all large Internet service providers manage their networks. Many of them use the same or similar tools that Trapper.io does. If the company didn’t manage its network, its customers would be subject to the negative effects of spam, viruses, security attacks, network congestion, and other risks and degradations of service. By engaging in responsible network management including enforcement of this Policy, Trapper.io can deliver the best possible remote DSL experience to all of its customers.
How does Trapper.io manage its network?
Trapper.io uses various tools and techniques to manage its network, deliver the Service, and ensure compliance with this Policy and the Subscriber Agreement. These tools and techniques are dynamic, like the network and its usage, and can and do change frequently. For example, these network management activities may include (i) identifying spam and preventing its delivery to customer e-mail accounts, (ii) detecting malicious Internet traffic and preventing the distribution of viruses or other harmful code or content, (iii) temporarily lowering the priority of traffic for users who are the top contributors to current network congestion, and (iv) using other tools and techniques that Trapper.io may be required to implement in order to meet its goal of delivering the best possible remote DSL experience to all of its customers.
Terms of Payments and Refunds
Full upfront payment is required to obtain the service. Payment amount is defined by the plan that was chosen for the service. If payment is on hold by payment processing merchant or involved in dispute, Trapper.io reserves the right to suspend or terminate an account without any further refund and also might blacklist such customer from purchasing any further services. Trapper.io reserves the right to provide only store credit, which can be used towards future purchases of its services. No refunds provided.
Are there any more restrictions that apply to the Service?
You must ensure that your use of the Service does not restrict, inhibit, interfere with, or degrade any other person’s use of the Service, nor represent (as determined by Trapper.io in its sole discretion) an overly large burden on the network. In addition, you must ensure that your use of the Service does not limit or interfere with Trapper.io ability to deliver and monitor the Service or any part of its network. If you use the Service in violation of the restrictions referenced above, that is a violation of this Policy. In these cases, Trapper.io may, in its sole discretion, suspend or terminate your Service account or request that you subscribe to a version of the Service (such as a commercial grade Internet service, if appropriate) if you wish to continue to use the Service at higher data consumption levels. Trapper.io may also provide versions of the Service with different speed and data consumption limitations, among other characteristics, subject to applicable Service plans. Trapper.io determination of the data consumption for Service accounts is final.
IV. Violation of this Acceptable Use Policy
What happens if you violate this Policy?
Trapper.io reserves the right immediately to suspend or terminate your Service account and terminate the Subscriber Agreement if you violate the terms of this Policy or the Subscriber Agreement.
How does Trapper.io enforce this Policy?
Trapper.io does not routinely monitor the activity of individual Service accounts for violations of this Policy, except for determining aggregate data consumption in connection with the data consumption provisions of this Policy. However, in the company’s efforts to promote good citizenship within the Internet community, it will respond appropriately if it becomes aware of inappropriate use of the Service. Trapper.io has no obligation to monitor the Service and/or the network. However, Trapper.io and its suppliers reserve the right at any time to monitor bandwidth, usage, transmissions, and content in order to, among other things, operate the Service; identify violations of this Policy; and/or protect the network, the Service and Trapper.io users.
Trapper.io prefers to inform customers of inappropriate activities and give them a reasonable period of time in which to take corrective action. Trapper.io also prefers to have customers directly resolve any disputes or disagreements they may have with others, whether customers or not, without Trapper.io intervention. However, if the Service is used in a way that Trapper.io or its suppliers, in their sole discretion, believe violates this Policy, Trapper.io or its suppliers may take any responsive actions they deem appropriate under the circumstances with or without notice. These actions include, but are not limited to, temporary or permanent removal of content, cancellation of newsgroup posts, filtering of Internet transmissions, and the immediate suspension or termination of all or any portion of the Service (including but not limited to newsgroups). Neither Trapper.io nor its affiliates, suppliers, or agents will have any liability for any of these responsive actions. These actions are not Trapper.io exclusive remedies and Trapper.io may take any other legal or technical actions it deems appropriate with or without notice.
Trapper.io reserves the right to investigate suspected violations of this Policy, including the gathering of information from the user or users involved and the complaining party, if any, and examination of material on Trapper.io servers and network. During an investigation, Trapper.io may suspend the account or accounts involved and/or remove or block material that potentially violates this Policy. You expressly authorize and consent to Trapper.io and its suppliers cooperating with (i) law enforcement authorities in the investigation of suspected legal violations, and (ii) and system administrators at other Internet service providers or other network or computing facilities in order to enforce this Policy. Upon termination of your Service account, Trapper.io is authorized to delete any files, programs, data, e-mail and other messages associated with your account (and any secondary accounts).
The failure of Trapper.io or its suppliers to enforce this Policy, for whatever reason, shall not be construed as a waiver of any right to do so at any time. You agree that if any portion of this Policy is held invalid or unenforceable, that portion will be construed consistent with applicable law as nearly as possible, and the remaining portions will remain in full force and effect. You agree to indemnify, defend and hold harmless Trapper.io and its affiliates, suppliers, and agents against all claims and expenses (including reasonable attorney fees) resulting from any violation of this Policy. Your indemnification will survive any termination of the Subscriber Agreement.
Trapper.io reserves the right to terminate any account at any time without any refund if we investigate and find out any violation of these terms of use.
V. Copyright and Digital Millennium Copyright Act Requirements
What is Trapper.io DMCA policy?
Trapper.io is committed to complying with U.S. copyright and related laws, and requires all customers and users of the Service to comply with these laws. Accordingly, you may not store any material or content on, or disseminate any material or content over, the Service (or any part of the Service) in any manner that constitutes an infringement of third party intellectual property rights, including rights granted by U.S. copyright law. Owners of copyrighted works who believe that their rights under U.S. copyright law have been infringed may take advantage of certain provisions of the Digital Millennium Copyright Act of 1998 (the “DMCA”) to report alleged infringements. It is Trapper.io policy in accordance with the DMCA and other applicable laws to reserve the right to terminate the Service provided to any customer or user who is either found to infringe third party copyright or other intellectual property rights, including repeat infringers, or who Trapper.io, in its sole discretion, believes is infringing these rights. Trapper.io may terminate the Service at any time with or without notice for any affected customer or user.
How do copyright owners report alleged infringements to Trapper.io?
Copyright owners may report alleged infringements of their works that are stored on the Service or the Personal Web Features by sending Trapper.io authorized agent a notification of claimed infringement that satisfies the requirements of the DMCA. Upon Trapper.io receipt of a satisfactory notice of claimed infringement for these works, Trapper.io will respond expeditiously to either directly or indirectly (i) remove the allegedly infringing work(s) stored on the Service or the Personal Web Features or (ii) disable access to the work(s). Trapper.io will also notify the affected customer or user of the Service of the removal or disabling of access to the work(s).
Copyright owners may send Trapper.io a notification of claimed infringement to report alleged infringements of their works to:
Email: info (at) Trapper (dot) io
Copyright owners may use their own notification of claimed infringement form that satisfies the requirements of Section 512(c)(3) of the U.S. Copyright Act. Under the DMCA, anyone who knowingly makes misrepresentations regarding alleged copyright infringement may be liable to Trapper.io, the alleged infringer, and the affected copyright owner for any damages incurred in connection with the removal, blocking, or replacement of allegedly infringing material.
What can customers do if they receive a notification of alleged infringement?
If you receive a notification of alleged infringement as described above, and you believe in good faith that the allegedly infringing works have been removed or blocked by mistake or misidentification, then you may send a counter notification to Trapper.io. Upon Trapper.io receipt of a counter notification that satisfies the requirements of DMCA, Trapper.io will provide a copy of the counter notification to the person who sent the original notification of claimed infringement and will follow the DMCA’s procedures with respect to a received counter notification. In all events, you expressly agree that Trapper.io will not be a party to any disputes or lawsuits regarding alleged copyright infringement.
If a notification of claimed infringement has been filed against you, you can file a counter notification with Trapper.io designated agent using the contact information shown above. All counter notifications must satisfy the requirements of Section 512(g)(3) of the U.S. Copyright Act.
Revised and effective: February 07, 2017